Siemens는 자동차 임베디드 소프트웨어 와 임베디드 소프트웨어 엔지니어링 솔루션을 모두 제공합니다. Siemens는 2023년 11월 Nucleus, Nucleus Hypervisor, Nucleus ReadyStart, Sokol Flex Linux, Sokol Omni Linux 및 Sourcery CodeBench 제품(관련 애드온 포함)의 사용 중지와 함께 SoC용 독립형 임베디드 소프트웨어 제공을 중단했습니다. 이러한 제품에 대한 기존 지원 계약은 여전히 유지되고 있으며, 자세한 내용은 Siemens 지원 센터에 문의하십시오.
임베디드 소프트웨어의 다양한 유형과 그 목적은 무엇입니까?
- 운영 체제 – 가장 일반적인 의미에서 운영 체제(OS)는 사용자가 컴퓨팅 장치에서 다른 응용 프로그램을 실행할 수 있도록 하는 소프트웨어입니다. 운영 체제는 키보드 및 마우스와 같은 입력 장치, 디스플레이 또는 프린터와 같은 출력 장치, 네트워크 연결 및 하드 드라이브 및 메모리와 같은 저장 장치를 포함한 프로세서의 하드웨어 리소스를 관리합니다. OS는 또한 소프트웨어 응용 프로그램의 효율적인 실행 및 관리와 메모리 할당을 용이하게 하는 서비스를 제공합니다.
- 펌웨어 – 펌웨어는 하드웨어용으로 직접 작성된 소프트웨어 유형입니다. API, 운영 체제 또는 장치 드라이버를 거치지 않고 작동하므로 다른 장치와 통신하거나 기본 작업 및 기능을 의도한 대로 수행하는 데 필요한 지침과 지침을 제공합니다.
- 미들웨어 – 미들웨어는 응용 프로그램과 운영 체제 사이에 위치한 소프트웨어 계층입니다. 미들웨어는 다음을 제공하여 소프트웨어 개발을 단순화하는 분산 시스템에서 자주 사용됩니다.
- 분산 응용 프로그램의 복잡성 숨기기
- 하드웨어, 운영 체제 및 프로토콜의 이질성 마스킹
- 상호 운용 가능하고 재사용 가능하며 이식 가능한 응용 프로그램을 만드는 데 사용되는 균일하고 높은 수준의 인터페이스를 제공합니다.
- 중복 작업을 최소화하고 응용 프로그램 간의 협업을 강화하는 공통 서비스 집합 제공
- 응용 프로그램 – 최종 사용자는 운영 체제에서 실행되고, 미들웨어 및 펌웨어를 사용하거나 상호 작용하며, 임베디드 시스템의 대상 기능의 주요 초점인 최종 소프트웨어 응용 프로그램을 개발합니다. 각 최종 응용 프로그램은 고유하지만 운영 체제와 펌웨어는 장치마다 동일할 수 있습니다.
임베디드 소프트웨어 vs 임베디드 시스템
임베디드 소프트웨어를 실행하는 장치 내의 하드웨어 구성 요소를 "임베디드 시스템"이라고 합니다. 임베디드 시스템에 사용되는 하드웨어 구성 요소의 몇 가지 예로는 전원 공급 회로, 중앙 처리 장치, 플래시 메모리 장치, 타이머 및 직렬 통신 포트가 있습니다. 장치의 초기 설계 단계에서 임베디드 시스템을 구성할 하드웨어와 장치 내 구성이 결정됩니다. 그런 다음 임베디드 소프트웨어가 처음부터 개발되어 정확한 구성으로 해당 하드웨어에서만 실행됩니다. 따라서 임베디드 소프트웨어 설계는 하드웨어 기능과 컴퓨터 프로그래밍에 대한 깊은 지식이 필요한 전문 분야입니다.
임베디드 소프트웨어 기반 기능의 예
회로 기판과 컴퓨터 칩이 있는 거의 모든 장치에는 이러한 구성 요소가 임베디드 소프트웨어 시스템에 배열되어 있습니다. 그 결과, 임베디드 소프트웨어 시스템은 일상 생활의 유비쿼터스이며 소비자, 산업, 자동차, 항공 우주, 의료, 상업, 통신 및 군사 기술 전반에 걸쳐 발견됩니다.
임베디드 소프트웨어 기반 기능의 일반적인 예는 다음과 같습니다.
- 의료 영상 장비에서 볼 수 있는 이미지 처리 시스템
- 항공기에서 볼 수 있는 Fly-by-wire 제어 시스템
- 보안 카메라의 동작 감지 시스템
- 신호등에서 볼 수 있는 교통 제어 시스템
- 스마트 홈 장치에서 볼 수 있는 타이밍 및 자동화 시스템
임베디드 시스템에는 어떤 종류가 있나요?
성능 및 기능 요구 사항에 따라 임베디드 시스템에는 5가지 주요 클래스가 있습니다.
- 실시간 임베디드 시스템은 결정적이고 반복 가능한 방식으로 작업을 완료하며, 이는 운영 체제의 기본 아키텍처 및 스케줄링뿐만 아니라 스레드 성능, 분기 및 인터럽트 지연 시간의 영향을 받습니다. 범용 임베디드 시스템에는 실시간 요구 사항이 포함되어 있지 않으며 완료 시간에 대한 종속성 없이 인터럽트 또는 분기를 관리할 수 있습니다. 그래픽 디스플레이와 키보드 및 마우스 관리는 일반 시스템의 좋은 예입니다.
- 독립형 임베디드 시스템은 호스트 시스템이나 외부 처리 리소스 없이 작업을 완료할 수 있습니다. 연결된 장치에서 데이터를 출력하거나 수신할 수 있지만 작업을 완료하기 위해 장치에 의존하지는 않습니다.
- 독립형 임베디드 시스템은 호스트 시스템이나 외부 처리 리소스 없이 작업을 완료할 수 있습니다. 연결된 장치에서 데이터를 출력하거나 수신할 수 있지만 작업을 완료하기 위해 장치에 의존하지는 않습니다.
- 네트워크로 연결된 임베디드 시스템은 연결된 네트워크에 의존하여 할당된 작업을 수행합니다.
- 시스템 하드웨어 아키텍처의 복잡성에 따라 임베디드 시스템에는 세 가지 주요 유형이 있습니다. 네트워크로 연결된 임베디드 시스템은 연결된 네트워크에 의존하여 할당된 작업을 수행합니다.
최종 시장이 임베디드 시스템에 미치는 영향
임베디드 시스템 요구 사항 및 구성 요소는 목표 시장의 요구 사항에 따라 다릅니다. 몇 가지 예는 다음과 같습니다.
- 소비자 – 세탁기, 웨어러블 장치 및 휴대폰과 같은 소비재와 같은 응용 분야에서 임베디드 시스템은 축소된 크기를 강조합니다.
- 시스템 온 칩, 저전력 소비 또는 배터리 작동 및 그래픽 인터페이스. 이러한 응용 분야에서는 구성 가능한 운영 체제와 설계의 작동하지 않는 "도메인"을 차단할 수 있는 기능이 중요합니다.
- 네트워킹 – 엔터프라이즈 네트워크의 연결, 통신, 운영 및 관리를 가능하게 하는 애플리케이션입니다. 사용자, 프로세스, 애플리케이션, 서비스 및 외부 네트워크/인터넷 간의 통신 경로와 서비스를 제공합니다. 임베디드 네트워크 애플리케이션은 응답 속도, 패킷 처리 및 주변 장치 하드웨어 경로에 중점을 둡니다.
- 산업 – 공장 현장 관리, 모터 및 풍차와 같은 애플리케이션의 경우 클라우드 연결 및 결정론적 "실시간" 운영을 보호하는 경향이 있으며 미들웨어에 중점을 둘 수 있습니다.
- 의료, 자동차 및 항공우주 – 이러한 산업에는 최종 사용자에게 해를 끼치지 않으면서(안전) 필요한 데이터만 시스템에 들어오거나 나가도록 보장(보안)하기 위해 설계의 일부가 서로 격리되는 혼합 안전이 중요한 시스템이 필요합니다. 자동차 및 의료 기기의 자율 주행 시스템을 예로 들 수 있습니다. 이러한 임베디드 시스템은 오픈 소스(Linux)와 결정론적 실시간 운영 체제(RTOS)를 혼합하여 사용할 수 있으며 검증된 미들웨어를 많이 활용합니다.
오토모티브 임베디드 소프트웨어가 다른 이유는 무엇입니까?
자동차 전자 장치에서는 제동, 조향, 서스펜션, 파워트레인 등과 같은 기능을 각각 제어하는 여러 임베디드 시스템에서 복잡한 실시간 상호 작용이 발생합니다. 각 임베디드 시스템을 포함하는 물리적 하우징을 전자 제어 장치(ECU)라고 합니다. 각 ECU와 임베디드 소프트웨어는 분산 시스템으로 알려진 복잡한 전기 아키텍처의 일부입니다.
차량의 분산 시스템을 구성하는 ECU는 서로 통신함으로써 자동 비상 제동, 어댑티브 크루즈 컨트롤, 스태빌리티 컨트롤, 어댑티브 헤드라이트 등과 같은 다양한 기능을 실행할 수 있습니다. 단일 기능은 여러 네트워킹 프로토콜로 연결된 수많은 ECU에 분산된 20개 이상의 임베디드 소프트웨어 어플리케이션 간의 상호 작용이 필요할 수 있습니다. 임베디드 소프트웨어와 함께 배포된 복잡한 제어 알고리즘은 기능의 적절한 타이밍, 필요한 입력 및 출력, 데이터 보안을 보장합니다.
자동차 소프트웨어 애플리케이션 기반 기능의 일반적인 예는 다음과 같습니다.
- ADAS(첨단 운전자 보조 시스템) 어댑티브 크루즈 컨트롤, 자동 비상 제동, 차선 유지 보조, 교통 보조, 차선 이탈 경고와 같은 기능
- 배터리 관리
- 토크 보상
- 연료 분사 속도 제어
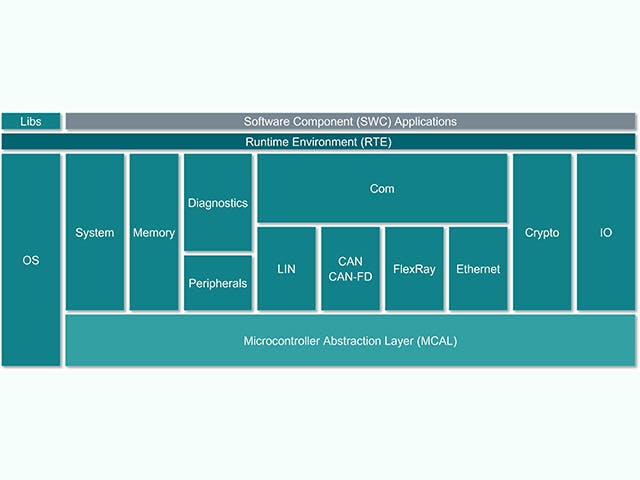
ECU 소프트웨어 스택
전자 제어 장치(Electronic Control Unit, ECU)는 칩 레벨 하드웨어와 임베디드 소프트웨어 스택이 있는 메인 컴퓨팅 유닛으로 구성됩니다. 그러나 자동차 제조업체들 사이에서는 단일 칩에 여러 컴퓨팅 코어를 포함하는 복잡한 집적 회로가 있는 ECU를 설계하는 추세가 증가하고 있습니다. 이러한 SoC는 하드웨어를 통합하기 위해 다수의 ECU 추상화를 호스팅할 수 있습니다. ECU를 위한 소프트웨어 스택에는 일반적으로 로우 레벨 펌웨어에서 하이 레벨 임베디드 소프트웨어 어플리케이션에 이르기까지 다양한 솔루션이 포함됩니다.
ECU 스택 | 설명 |
임베디드 소프트웨어 응용 프로그램 | 제어 알고리즘, 처리, 서비스 |
응용 프로그램 프레임워크 | 보안 및 안전 프레임워크 |
운영 환경 | AUTOSAR 클래식, AUTOSAR Adaptive, 입력/출력 채널 |
내장된 가상화 | 실시간 OS, ECU 추상화 |
펌웨어 | 부트로더, 보안 스토리지, 보안 스레딩 |
하드웨어 | 실리콘 기반 장치, 마이크로 컨트롤러, 단일 또는 다중 레이어 기판 |