Siemens propose à la fois des logiciels embarqués pour l’automobile et des solutions d’ingénierie logicielle embarquée . Siemens a cessé de proposer des logiciels embarqués autonomes pour les SoC avec le retrait en novembre 2023 des produits Nucleus, Nucleus Hypervisor, Nucleus ReadyStart, Sokol Flex Linux, Sokol Omni Linux et Sourcery CodeBench (y compris les modules complémentaires associés). Les contrats d’assistance existants pour ces produits sont toujours honorés, veuillez contacter le centre d’assistance Siemens pour plus d’informations.
Quels sont les différents types de logiciels embarqués et leurs finalités ?
- Système d’exploitation – Un système d’exploitation (OS), dans son sens le plus général, est un logiciel qui permet à un utilisateur d’exécuter d’autres applications sur un appareil informatique. Le système d’exploitation gère les ressources matérielles d’un processeur, y compris les périphériques d’entrée tels qu’un clavier et une souris, les périphériques de sortie tels que les écrans ou les imprimantes, les connexions réseau et les périphériques de stockage tels que les disques durs et la mémoire. Le système d’exploitation fournit également des services pour faciliter l’exécution et la gestion efficaces des programmes d’application logicielle, ainsi que l’allocation de mémoire pour ceux-ci.
- Micrologiciel – Le micrologiciel est un type de logiciel qui est écrit directement pour un matériel. Il fonctionne sans passer par les API, le système d’exploitation ou les pilotes de périphériques, fournissant les instructions et les conseils nécessaires pour communiquer avec d’autres appareils ou effectuer des tâches et des fonctions de base comme prévu.
- Middleware – Le middleware est une couche logicielle située entre les applications et les systèmes d’exploitation. Le middleware est souvent utilisé dans les systèmes distribués où il simplifie le développement logiciel en fournissant les éléments suivants :
- Masquer les subtilités des applications distribuées
- Masquage de l’hétérogénéité du matériel, des systèmes d’exploitation et des protocoles
- Fournir des interfaces uniformes et de haut niveau utilisées pour créer des applications interopérables, réutilisables et portables.
- Fournir un ensemble de services communs qui minimisent la duplication des efforts et améliorent la collaboration entre les applications
- Application – L’utilisateur final développe l’application logicielle finale qui s’exécute sur le système d’exploitation, utilise ou interagit avec l’intergiciel et le micrologiciel, et constitue l’objectif principal de la fonction cible des systèmes embarqués. Chaque application finale est unique, tandis que les systèmes d’exploitation et le micrologiciel peuvent être identiques d’un appareil à l’autre.
Logiciels embarqués vs systèmes embarqués
Les composants matériels d’un appareil exécutant un logiciel embarqué sont appelés « système embarqué ». Quelques exemples de composants matériels utilisés dans les systèmes embarqués sont les circuits d’alimentation, les unités centrales de traitement, les périphériques de mémoire flash, les minuteries et les ports de communication série. Au cours des premières phases de conception d’un appareil, le matériel qui composera le système embarqué – et sa configuration au sein de l’appareil – est décidé. Ensuite, le logiciel embarqué est développé à partir de zéro pour fonctionner exclusivement sur ce matériel dans cette configuration précise. Cela fait de la conception de logiciels embarqués un domaine spécialisé nécessitant une connaissance approfondie des capacités matérielles et de la programmation informatique.
Exemples de fonctions logicielles embarquées
Presque tous les appareils équipés de cartes de circuits imprimés et de puces informatiques ont ces composants organisés dans un système logiciel embarqué. Par conséquent, les systèmes logiciels embarqués sont omniprésents dans la vie quotidienne et se retrouvent dans les technologies grand public, industrielles, automobiles, aérospatiales, médicales, commerciales, de télécommunications et militaires.
Voici quelques exemples courants de fonctionnalités logicielles embarquées :
- Systèmes de traitement d’images que l’on trouve dans les équipements d’imagerie médicale
- Systèmes de commande de vol électriques que l’on trouve dans les avions
- Systèmes de détection de mouvement dans les caméras de sécurité
- Systèmes de contrôle de la circulation dans les feux de circulation
- Systèmes de chronométrage et d’automatisation que l’on trouve dans les appareils domestiques intelligents
Quels sont les différents types de systèmes embarqués ?
En fonction des performances et des exigences fonctionnelles, il existe cinq grandes classes de systèmes embarqués :
- Les systèmes embarqués en temps réel effectuent des tâches de manière déterministe et reproductible, ce qui est affecté par l’architecture et la planification sous-jacentes des systèmes d’exploitation, ainsi que par les performances des threads, la duplication et la latence d’interruption. Les systèmes embarqués à usage général ne contiennent pas d’exigence en temps réel et peuvent gérer les interruptions ou les branchements sans dépendre d’un temps d’achèvement. Les écrans graphiques et la gestion du clavier et de la souris sont de bons exemples de systèmes généraux.
- Les systèmes embarqués autonomes peuvent effectuer des tâches sans système hôte ni ressources de traitement externes. Ils peuvent émettre ou recevoir des données à partir d’appareils connectés, mais ne dépendent pas d’eux pour accomplir leur tâche.
- Les systèmes embarqués autonomes peuvent accomplir leur tâche sans système hôte ni ressources de traitement externes. Ils peuvent émettre ou recevoir des données à partir d’appareils connectés, mais ne dépendent pas d’eux pour accomplir leur tâche.
- Les systèmes embarqués en réseau dépendent d’un réseau connecté pour effectuer les tâches qui leur sont assignées.
- En fonction de la complexité de l’architecture matérielle du système, il existe trois principaux types de systèmes embarqués : Les systèmes embarqués en réseau dépendent d’un réseau connecté pour effectuer les tâches qui leur sont assignées.
Comment les marchés finaux affectent-ils les systèmes embarqués ?
Les exigences et les composants des systèmes embarqués diffèrent en fonction des demandes du marché cible. En voici quelques exemples :
- Consommateur – Dans des applications telles que les biens de consommation tels que les lave-linge, les appareils portables et les téléphones portables, les systèmes intégrés mettent l’accent sur la taille réduite de la
- Système sur puce, faible consommation d’énergie ou fonctionnement sur batterie, et interfaces graphiques. Dans ces applications, les systèmes d’exploitation configurables et la possibilité de désactiver les « domaines » non opérationnels de la conception sont valorisés.
- Mise en réseau : applications qui permettent la connectivité, la communication, l’exploitation et la gestion d’un réseau d’entreprise. Il fournit le chemin de communication et les services entre les utilisateurs, les processus, les applications, les services et les réseaux externes/Internet. Les applications réseau embarquées se concentrent sur la vitesse de réponse, le traitement des paquets et les chemins matériels périphériques.
- Industriel – Pour des applications telles que la gestion d’usine, les moteurs et les éoliennes, l’accent est mis sur la sécurisation de la connectivité au cloud et le fonctionnement déterministe « en temps réel » et peut se concentrer fortement sur le middleware.
- Médical, automobile et aérospatiale – Ces industries ont besoin de systèmes critiques de sécurité mixtes, où les parties de la conception sont isolées les unes des autres pour garantir que seules les données nécessaires entrent ou sortent du système (sécurité) tout en garantissant l’absence de dommages à l’utilisateur final (sécurité). Les systèmes de conduite autonome dans les automobiles et les dispositifs médicaux en sont des exemples. Ces systèmes embarqués peuvent comporter un mélange de systèmes d’exploitation en temps réel (RTOS) open source (Linux) et déterministes et utilisent fortement des intergiciels éprouvés.
Pourquoi les logiciels embarqués automobiles sont-ils différents ?
Dans l’électronique automobile, des interactions complexes en temps réel se produisent entre plusieurs systèmes embarqués que chacun contrôle des fonctions telles que le freinage, la direction, la suspension, le groupe motopropulseur, etc. Le boîtier physique contenant chaque système embarqué est appelé unité de commande électronique (ECU). Chaque calculateur et son logiciel embarqué font partie d’une architecture électrique complexe connue sous le nom de système distribué.
En communiquant entre eux, les calculateurs qui composent le système distribué d’un véhicule peuvent exécuter une variété de fonctions, telles que le freinage d’urgence automatique, le régulateur de vitesse adaptatif, le contrôle de stabilité, les phares adaptatifs, et bien plus encore. Une seule fonction peut nécessiter des interactions entre 20 applications logicielles embarquées ou plus réparties sur de nombreux calculateurs connectés par plusieurs protocoles réseau. Des algorithmes de contrôle complexes déployés avec le logiciel embarqué garantissent la bonne synchronisation des fonctions, les entrées et sorties nécessaires et la sécurité des données.
Voici quelques exemples courants de fonctionnalités basées sur des applications logicielles automobiles :
- Fonctions ADAS (Advanced Driver Assist Systems) comme le régulateur de vitesse adaptatif, le freinage d’urgence automatique, l’assistance au maintien dans la voie, l’assistance à la circulation, les avertissements de sortie de voie
- Gestion de la batterie
- Compensation de couple
- Contrôle du débit d’injection de carburant
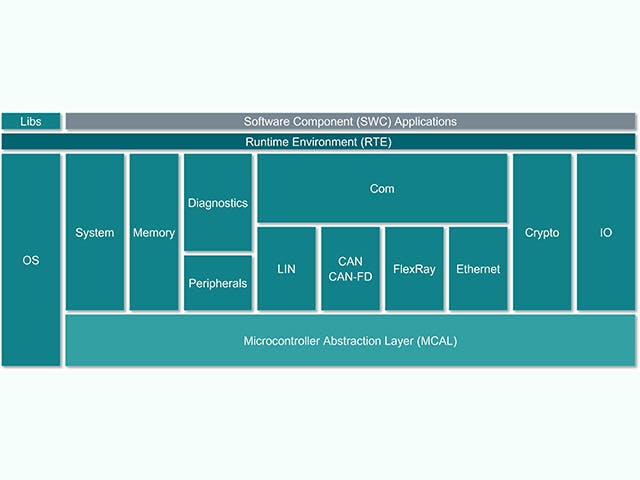
Pile logicielle du calculateur
L’unité de contrôle électronique ou ECU est composée d’une unité de calcul principale avec du matériel au niveau de la puce et d’une pile de logiciels embarqués. Cependant, les constructeurs automobiles ont de plus en plus tendance à concevoir des calculateurs avec des circuits intégrés complexes qui contiennent plusieurs cœurs de calcul sur une seule puce – ce que l’on appelle un système sur puce (SoC). Ces SoC peuvent héberger une multitude d’abstractions de calculateurs afin de consolider le matériel. La pile logicielle d’un calculateur comprend généralement une gamme de solutions, du micrologiciel de bas niveau aux applications logicielles embarquées de haut niveau.
Pile ECU | Description |
Application logicielle embarquée | Algorithmes de contrôle, traitements, services |
Cadre d’application | Cadres de sécurité et de sûreté |
Environnement d’exploitation | AUTOSAR classic, AUTOSAR Adaptive, Canaux d’entrées/sorties |
Virtualisations embarquées | Système d’exploitation en temps réel, abstractions de calculateur |
Microprogramme | Chargeurs d’amorçage, stockage sécurisé, threading sécurisé |
Matériel | Dispositifs à base de silicium, microcontrôleurs, cartes à une ou plusieurs couches |